Major Leak Exposes Secrets of Chinese Cyber Firm KnownSec
A large cache of internal documents from Chinese cybersecurity company KnownSec has leaked online, exposing details about its government projects, hacking tools, and global data collection efforts.
More than 12,000 files briefly appeared on GitHub before being taken down. Security researchers were able to access and review them, and the newest documents appear to be from 2023.
This suggests the data theft likely happened around that time or that the person who leaked it intentionally held back newer files.
It is not yet known who is responsible for the leak. It could be a former employee or an outside hacker. No group has claimed responsibility.
What KnownSec Actually Does
KnownSec is best known for ZoomEye, an online search engine that scans and maps connected devices across the internet.
It works in a similar way to other global scanning tools such as Shodan or Censys.
Behind the scenes, the company also works closely with Chinese military and intelligence agencies. The leaked files include internal documents about these contracts, tools built for surveillance, and data collected from organizations around the world.
Most of the tools mentioned in the leak are not exotic. They appear to be standard remote access tools and data analysis software, the same types used by law enforcement agencies everywhere.
The Target List
One of the most revealing parts of the leak is a spreadsheet listing 80 foreign organizations or systems from which KnownSec collected data.
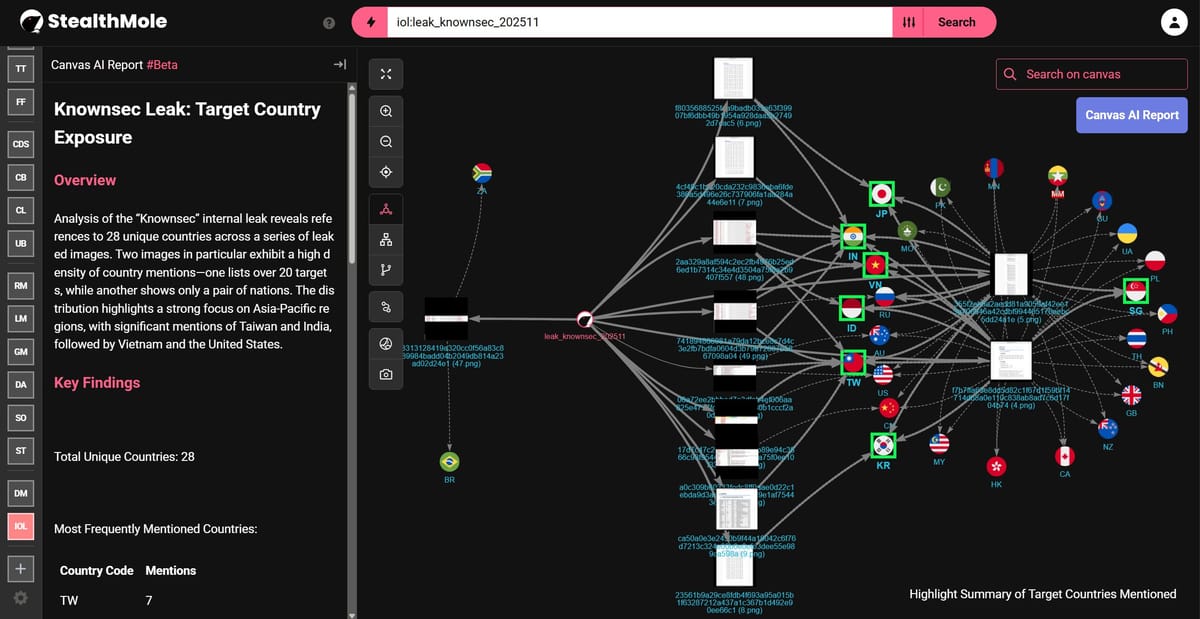
Researchers say KnownSec has mapped parts of the digital infrastructure of at least 28 countries.
This type of scanning is not unusual, but the leaked files show that the company went further by pulling data from unsecured servers when it found them.
Examples from the leaked data include:
• 95GB of immigration records from India
• 3TB of call logs from a South Korean telecom provider
• 459GB of transportation and road planning data from Taiwan
• Passwords for Yahoo accounts in Taiwan
• Data from LinkedIn users in Brazil
• Various datasets exposed through unprotected servers in multiple nations
This suggests that KnownSec was not just scanning the internet but actively harvesting whatever information was left exposed.
Highlight Summary of Target Countries Mentioned in the "Knownsec" Internal Leak
— Fusion Intelligence Center @ StealthMole (@stealthmole_int) November 11, 2025
An analysis of several sample materials from the Knownsec internal leak reveals that network reconnaissance and information-gathering activities were conducted across 28 countries.
The group also… pic.twitter.com/PaR9XgTL8d
How Serious Is This Leak
At first glance, this leak appears less explosive than a previous leak involving another Chinese contractor that directly connected that firm to state-backed hacking operations. Even so, the KnownSec leak is large, and it will take time for analysts to work through the full dataset.
As more findings emerge, it could reveal new insights into how commercial cybersecurity firms support national intelligence activities and how much data is at risk when organizations leave servers exposed online.



Comments ()