How to Avoid Being a Victim of Cybercrime: A Comprehensive Guide to Staying Safe Online
In an era where our lives are increasingly intertwined with technology, cybercrime has become a pervasive threat.
From stolen identities to ransomware locking critical files, cybercriminals exploit vulnerabilities in both systems and human behavior to wreak havoc.
The financial and emotional toll can be devastating, with global cybercrime costs projected to hit $10.5 trillion annually by 2025, according to Cybersecurity Ventures.

Fortunately, by understanding the most common types of cybercrime and adopting proactive defenses, you can significantly reduce your risk.
In this in-depth guide, we’ll explore the primary forms of cybercrime, their real-world impact, and practical, actionable steps to protect yourself in the digital age.
ON SURVIVAL is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.
Common Types of Cybercrime and How to Avoid Them
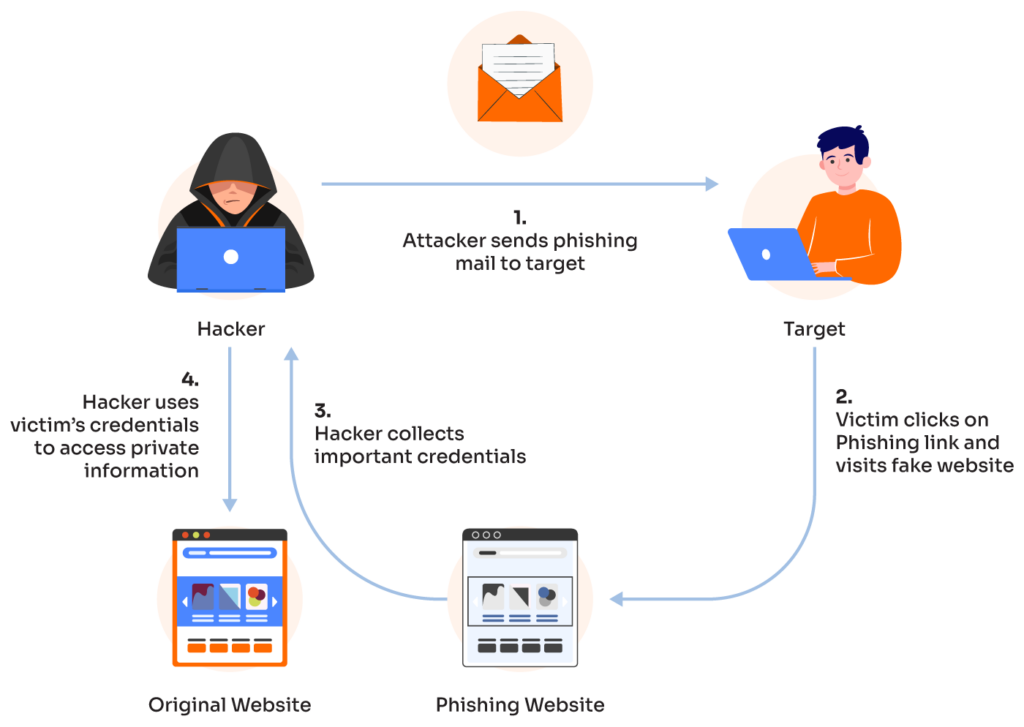
1. Phishing Attacks
What it is: Phishing is one of the most prevalent cybercrimes, where attackers send fraudulent emails, text messages, or other communications that mimic trusted sources.
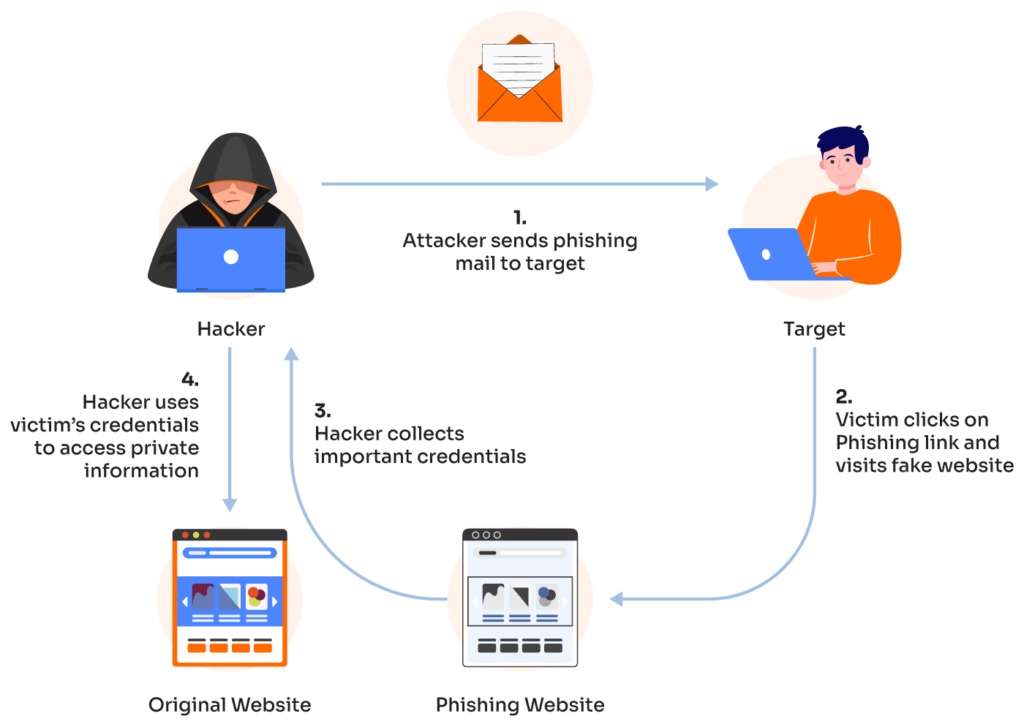
These messages often trick users into revealing sensitive information like login credentials or credit card numbers or clicking malicious links that install malware.
Phishing accounts for 36% of data breaches, per Verizon’s 2024 Data Breach Investigations Report.
Examples:
An email claiming to be from PayPal urging you to “update your account” links to a fake login page.
A text message with a link to “claim a prize” installs spyware on your phone.
How to Avoid Phishing:
Scrutinize the sender: Check the email address or phone number for subtle discrepancies (e.g., “service@netf1ix.com” instead of “service@netflix.com”). Even if the name looks legitimate, verify the domain.
Avoid clicking links impulsively: Hover over URLs to preview their destination. If it looks suspicious, don’t click. Instead, manually visit the official website.
Enable two-factor authentication (2FA): 2FA requires a second form of verification (e.g., a code sent to your phone), making stolen passwords less useful to attackers.
Leverage anti-phishing tools: Modern browsers like Chrome and email platforms like Gmail have built-in filters to flag suspicious messages. Consider third-party tools like Barracuda or Proofpoint for added protection.
Cultivate skepticism: Be wary of unsolicited messages, especially those creating urgency (“Your account will be suspended!”) or offering unrealistic rewards. When in doubt, contact the organization directly using verified contact information.
2. Identity Theft
What it is: Identity theft involves cybercriminals stealing personal information; such as Social Security numbers, bank account details, or login credentials; to impersonate you or commit fraud.
The Federal Trade Commission reported over 1.1 million identity theft cases in 2023 alone.
Examples:
A hacker uses your stolen credit card to make unauthorized purchases.
Someone opens a loan in your name using your personal details.
How to Avoid Identity Theft:
Monitor accounts regularly: Review bank statements, credit reports, and online accounts weekly for anomalies.
Free tools like Credit Karma or AnnualCreditReport.com can help track your credit.
Use strong, unique passwords: Create passwords with at least 12 characters, mixing letters, numbers, and symbols.
Never reuse passwords across sites. Password managers like LastPass, Dashlane, or 1Password simplify this process.
Freeze your credit: Contact Equifax, Experian, and TransUnion to freeze your credit, preventing unauthorized accounts from being opened in your name. This is especially useful if you’re not actively applying for credit.
Secure physical documents: Shred sensitive paperwork (e.g., bank statements, medical records) before disposal. Use a locked mailbox to prevent mail theft.
Limit oversharing: Avoid posting personal details—like your full birth date, address, or travel plans—on social media, as cybercriminals can use these to answer security questions or build trust.
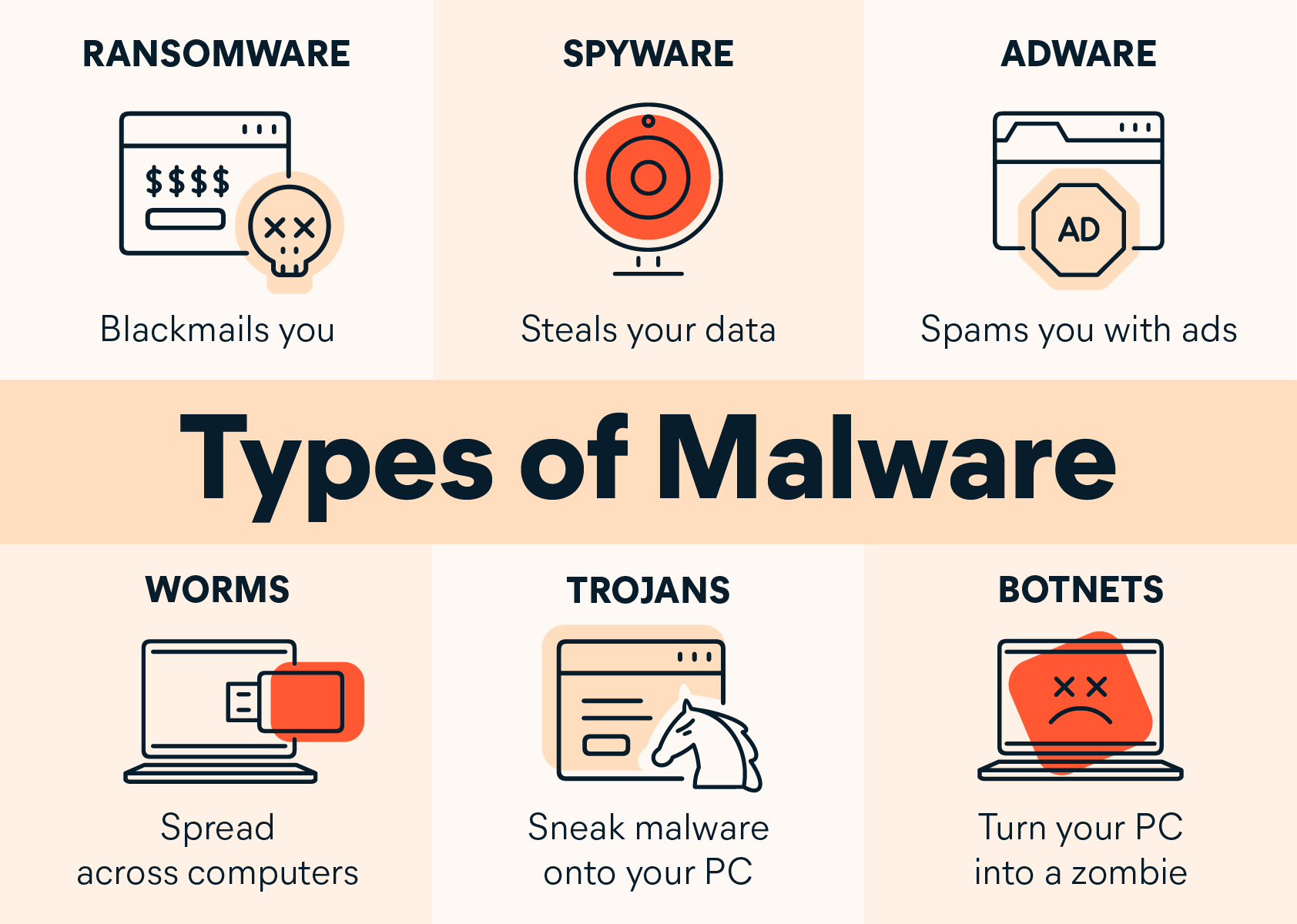
3. Malware Attacks
What it is: Malware (malicious software) encompasses viruses, ransomware, spyware, and trojans designed to damage devices, steal data, or extort money.
Ransomware, for instance, encrypts your files and demands payment for access, costing victims billions annually.
Examples:
A downloaded “free” app secretly logs your keystrokes to steal passwords.
Ransomware locks your business’s files, demanding cryptocurrency for decryption.
How to Avoid Malware:
Install trusted antivirus software: Programs like Norton, McAfee, or Bitdefender offer real-time protection against malware. Free options like Windows Defender are also effective for basic needs.
Update software religiously: Patch vulnerabilities by keeping your operating system, apps, and browsers up to date. Enable automatic updates where possible.
Avoid dubious downloads: Only download software from reputable sources, such as official app stores or verified websites.
Steer clear of pirated content or “cracked” software, which often harbors malware.
Back up critical data: Regularly back up files to an external drive or secure cloud service like Google Drive, Dropbox, or iCloud. This ensures you can recover data without paying a ransom.
Enable a firewall: Use your device’s built-in firewall or a third-party solution to block unauthorized access to your system.
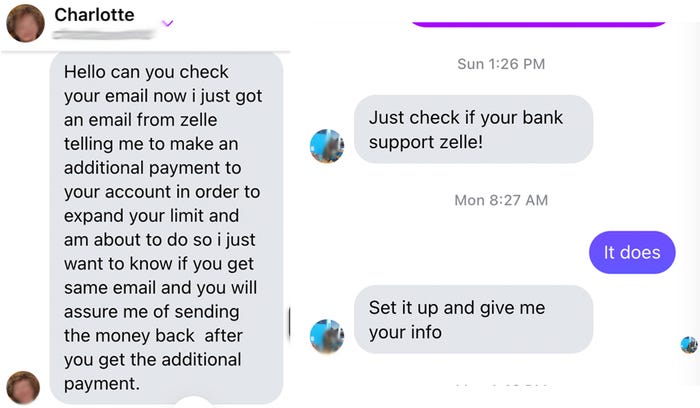
4. Online Scams
What it is: Online scams deceive users into sending money or sharing information through fake websites, investment schemes, romance scams, or fraudulent sales.
These scams often exploit emotional triggers like greed or sympathy.
Examples:
A fake online store advertises discounted electronics but never delivers.
A “romance” scammer builds a months-long relationship, then requests money for a fabricated emergency.
How to Avoid Online Scams:
Research vendors: Before buying, check reviews on platforms like Trustpilot or the Better Business Bureau. Use Google’s Safe Browsing tool (transparencyreport.google.com) to verify website legitimacy.
Avoid untraceable payments: Be cautious of requests for wire transfers, gift cards, or cryptocurrency, as these are nearly impossible to recover. Stick to credit cards or PayPal for buyer protection.
Trust your gut: If a deal seems too good to be true or someone pressures you to act fast, step back and verify.
Stay educated: Follow scam alerts from the Federal Trade Commission (consumer.ftc.gov) or local consumer protection agencies to recognize emerging tactics.
Secure transactions: Shop on websites with “https://” and a padlock icon, indicating encrypted connections.
5. Social Engineering
What it is: Social engineering manipulates people into divulging confidential information or performing compromising actions.
It exploits psychological vulnerabilities like trust, fear, or curiosity.
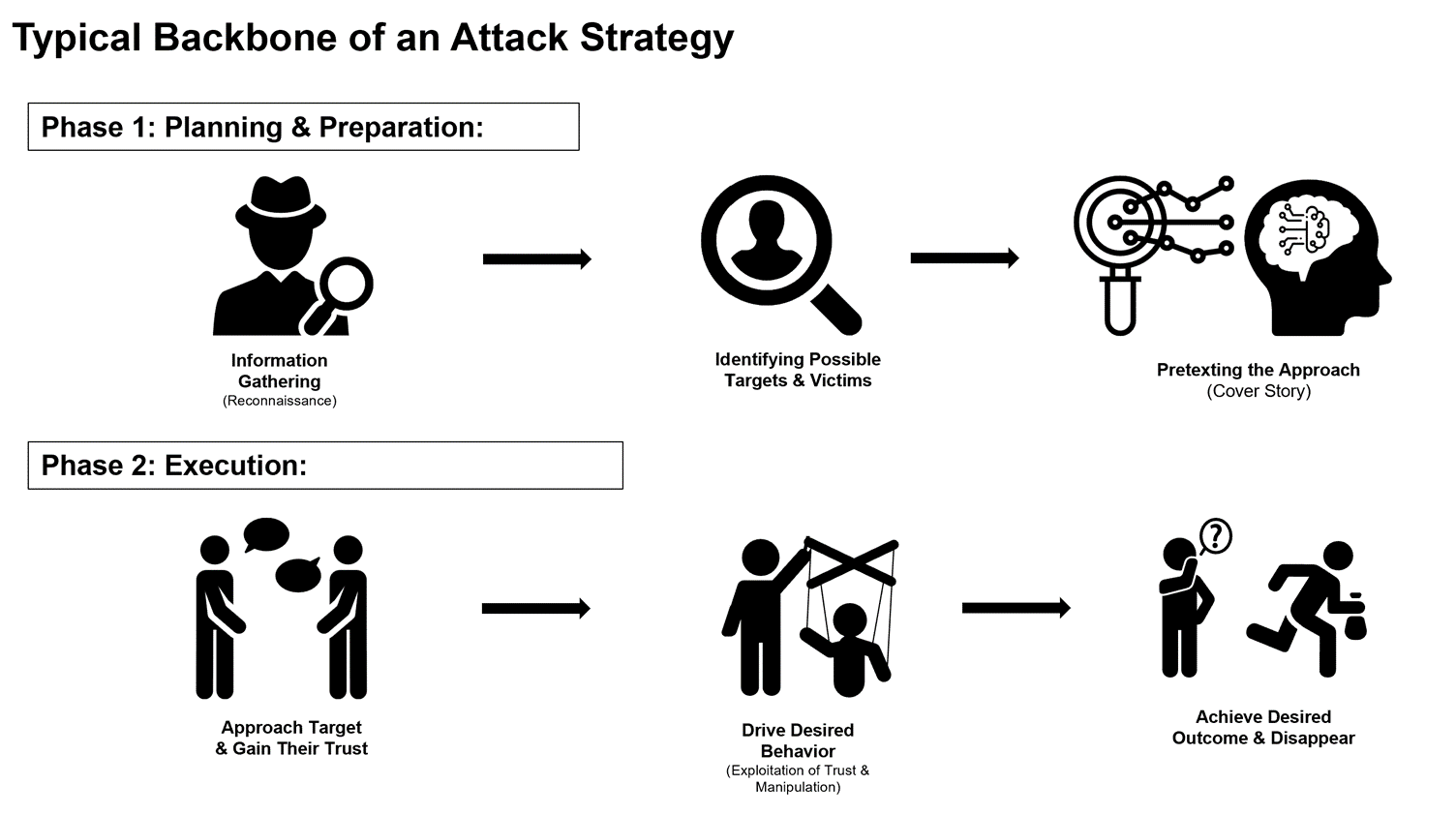
Examples:
A scammer posing as IT support claims your computer is infected and requests remote access.
A fraudster impersonates a colleague via email, asking for sensitive company data.
How to Avoid Social Engineering:
Verify identities: If someone contacts you claiming authority, hang up and call back using an official number from the organization’s website.
Limit public information: Restrict what you share on social media (e.g., pet names, favorite books) to prevent scammers from cracking security questions.
Question unsolicited requests: Be skeptical of unexpected calls, emails, or visits, especially those demanding immediate action.
Use privacy settings: Lock down social media profiles to limit what strangers can access. Regularly review who can see your posts.
Report attempts: Alert your employer, bank, or authorities if you encounter suspicious behavior, as it may protect others.
6. Data Breaches
What it is: Data breaches occur when hackers infiltrate a company’s database, exposing user information like emails, passwords, or financial details.
The 2023 AT&T breach, for example, exposed data of millions of customers.
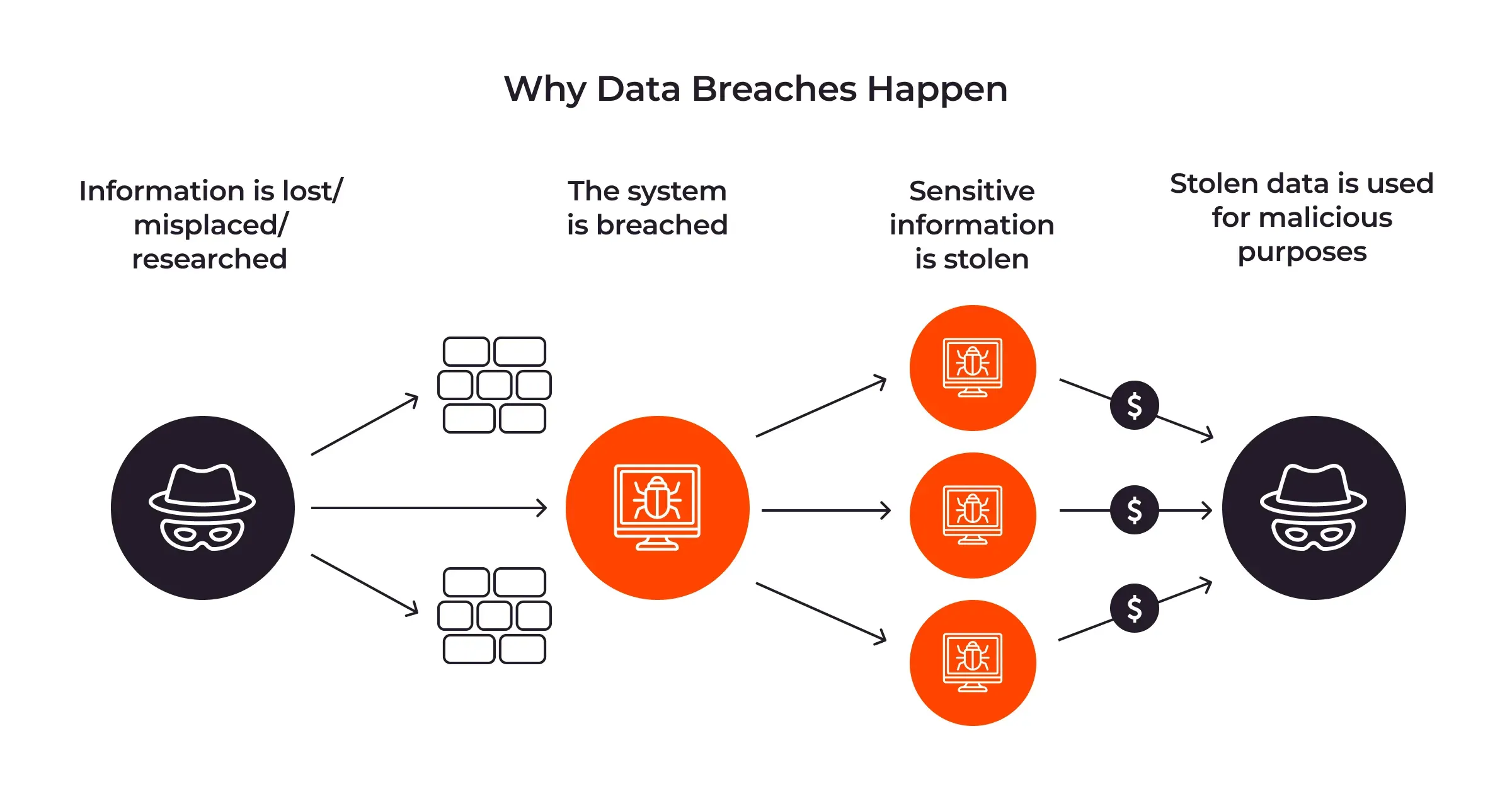
Examples:
A retailer’s hacked database leaks customer payment information.
A social media platform exposes user emails, enabling targeted phishing.
How to Avoid Data Breach Fallout:
Use unique passwords: If a breached site reuses your password, hackers can access other accounts. Password managers ensure each account has a distinct password.
Monitor breach alerts: Services like Have I Been Pwned (haveibeenpwned.com) notify you if your email appears in a breach, prompting timely action.
Act swiftly: If a breach occurs, change affected passwords immediately, enable 2FA, and monitor accounts for suspicious activity.
Assume exposure: Proactively freeze your credit and use encrypted tools like Signal for sensitive communications.
Choose secure platforms: Favor companies with robust security, such as end-to-end encryption or regular third-party audits.
General Tips for Cyber Safety
To fortify your defenses across all threats:
Stay informed: Follow cybersecurity blogs like Krebs on Security or government resources like the Cybersecurity and Infrastructure Security Agency (cisa.gov).
Use a VPN: A virtual private network (e.g., NordVPN, ExpressVPN) encrypts your internet connection, especially on public Wi-Fi networks.
Educate your circle: Share these tips with family, friends, or coworkers to foster a safer digital ecosystem.
Act decisively: If you suspect a cybercrime, report it to the FBI’s Internet Crime Complaint Center (ic3.gov), your bank, or local authorities, and secure your accounts immediately.
Invest in education: Consider online cybersecurity courses from platforms like Coursera or Udemy to deepen your knowledge.
Conclusion
Cybercrime is an ever-evolving challenge, but you’re not powerless.
By understanding phishing, identity theft, malware, scams, social engineering, and data breaches; and implementing the strategies outlined above;you can navigate the digital world with confidence.
The key is vigilance: stay informed, question the unexpected, and prioritize security in every online interaction.
Protect yourself today, an d you’ll avoid the costly consequences of cybercrime tomorrow.
Call to Action
Share this guide with someone who needs to stay cyber-safe, and subscribe for more insights on thriving in the digital age.
ON SURVIVAL is a reader-supported publication. To receive new posts and support my work, consider becoming a free or paid subscriber.



Comments ()